Introduction
The goal of this project was to put theorical knowledge into practice by doing a small uncomplicated project such as dumping the firmware from a router. This blog is a personal passion project of mine for me to show off any projects I working/worked on and have all of them in a centralized location to display everything.
Goals
The goal of this project extract the firmware from the MX25L1606E located on the F7D2301 v1 model of the Belkin N833 router.
Finding a target
Before the exploiting of devices and the questioning of life choices can begin we must first find a target device for this project.
After some research I stumbled upon a interesting article by cyber arc which did a ok job of explaining how to dump the firmware of a device and what tools would be needed. So after about a week of researching and comparing prices and reviews on various web retailers, it was decided
that the target would be a belkin N300 router due to a number of factors, such as its old age meant
- fits within my budget
- limited security measures
- easily replaceable
figure 1- image of the FK1002v3 model of the router
Thanks to the second hand market I managed to find brand new box still had the plastic wrapping on (sorry turtles) for £10 which fits within my budget of £25.
The firmware on this device is over 10 years, and has no security measures.
There's a lot of these on the second hand market meaning if I screw something up then its not the end of the world since there are plenty of these devices on the second hand market.
Cracking the case wide open
Now on to arguably the best part of hardware research. Breaking things. Typically my process involves searching around too see if anyone created a guide on how to open a device before on sites such as Youtube,ifixit,Reddit but after some searching nothing turned up. So back to the old fashioned way of pulling on it and hoping you don't hear a snap.
Thanks to the American Federal Communications Commission(FCC) which requires any device that operates within radio frequency band and is sold within the United States of America to have one, The number is used for monitoring emissions and certification purposes, making sure devices don't interfere with each other etc etc.

figure 2- pin configuration diagram of 8-pin SOP package for the MX25L1606E Flashchip from datasheet
As part of this, the company is also required to provide images such as the one above, which show both the external and internal workings of the device. Very useful and saves a lot of time, and money so know what you getting yourself into and if your project is even possible to start with.
Armed with those photos, and a ifixit opening kit. I stuck on a long rambling video SA about a topic I knew nothing about and got to work.
Over the next 20 or so minutes I learnt many things, I will summarize the main points for you.
- Having a plastic shell clamp shut on your finger when your aren't expecting it hurts a lot,
- A torch makes a excellent prop to both hold open the shell and provide lights so you can get to the clips right at the back, as seen below.

figure 3- hardware set up used to extract firmware out of the F9K1002v3 model router
Keeping the shell intact was critical since I will likely sell this device after Im finished with it to fund further projects.
Once the board had been Exhumed from the shell, I learnt another valuable lesson, as the eagle-eyed among you might have noticed this board does not match the board in the FCC image above. Thats because I bought the wrong model of this router. Which doesn't have the specific chip that i'm after.
A quick search through the FCC database for this line of device I found the correct device, and order it from ebay for cheap since its still quite a older device.
figure 4- router internals after internal metal sheilding has been removed
I wanted to include this error in the write-up since I think its valuable to show both the mistakes and the successes of projects as thats what I wish I had when I started, searching for the right model and trying to match the correct device by the images was fun, it taught be how to efficiently search second hand markets which I wouldn't have done if it was not for this mistake.
Communication is key
After about a week the correct model had arrived I cracked open the shell and was good for going again.
Finding the chip where it was suppose to be and being able to read off the ID number that's engraved on it, in order to find the data sheet which shows which pin outputs which signal and other important factors to communicate with with the router luckily everything was set to the typical rates of 9600/8N1) which is 9600 bits a second with 8 bits in a bytes, no parity bits and one stop bit encase anyone was wondering.
figure 5- The image above shows the wiring diagram from the MX25L1606E
data-sheet that was used to wire it up to the bus pirate
The set up you see below is the one that was used for dumping the contents of the flash chip, allow me to explain.
The wires that connect the flash chip to the bus pirate which was used to convert the Serial Peripheral Interface(SPI) into the Universial serial bus(usb) protocol which could then be passed through to the VM running on my pc that, had a tool called flashrom that allows for reading,writing,erasing,indenitfiying along with many more functions of various types of chips such as the one above.
Using the command "flashrom -p buspirate_spi:dev=/dev/ttyUSB0 -c MX25L1605A/MX25L1606E/MX25L1608E -r N833-dump1.bin", I told flashrom to use -p set the programer device(the bus pirate) using Spi that was on USB port 0 then use -c to try to dump the contents of one of thoses chips then use -r to save the extracted data as a binary(.bin) file called N833-dump.bin .
figure 6- pin configuration diagram of 8-pin SOP package
for the MX25L1606E Flashchip from datasheet
To steal a phrase from Marstian landings the 7 minutes of terror has started since at this point, there wasn't anything I could do besides wait. All the effort and resources I put into the project, were about bare fruit or go sour, and go sour they did, the bus pirate firmware needed to be upgraded to a newer version, simple right.
all I had to do was follow a tutorial on their github and download compile it, and stop me if your heard this one before but it didn't go to plan and it broke, because for some reason my bus pirate kept tripling the voltage regulation light which was odd because when I checked the voltage with a multi meter, it remained within spec the whole time and I hadn't had the issue before I flashed new firmware on to it.
After 2 weeks of debugging on and off, I decided to cut my losses and just use a older version of the firmware(6.3). Once that had been flashed on the bus pirate and everything had been set up again. It was time to endure the 7 minutes of terror again but this time it worked surprisingly first time. When I ran the file through cat and bin walk there was data there not just null zeros. The firmware was dumped a two more times in a mixture of disbelief and also to make sure it had been dumped correctly the first time.
Brief static analysis
While this section is a is part of a septate project I am working on I thought it would be remise of me not to show the complete process so this will just be a overview of the Static analysis I conducted.
figure 7- Using Binwalk to analysis the binary file entropy.
As you can see a 75% of the file has extremely high entropy which means the binary is likely either encrypted or compressed where as the other 25% as quite low entropy which means its likely just raw files
high entropy = more random
low entropy = less random
Now time to confirm or deny our findings by using binwalk -e dump.bin the same command but with a lower case e that will extract the files instead of analyzing their entropy.
figure 8- Data that had been extracted from the MX25L1606E chip through binwalk and the setup seen prviously
figure 9- extracted contents of the firmware
Looks like our theory has been confirmed around 50% of the contents of the binary seems to be the compressed in a 7zip file format, which makes life easy for us since its a extremely common format
figure 10- 10 largest file within the extracted firmware
For an initial quick analysis it made sense to look for the biggest files on hence the use of ls -Sl which sorts all the extracted files by size from biggest to smallest, currently were only interested in the biggest files so we used also ran the head command to limit the search to 10 files(searches start at 2 because computers are weird).
Running the strings command which searches for any minimum of 4 connected letters then piping that into a text file since the output usually gets cut off by the terminal maximum output length and makes searching for words of interest such as Linux,Kernal,verison super easy with the use of in terminal editors such as Nano.
figure 11- Strings command used to extract any string over 4 charaters in length from the file 22C10
then save into strings.txt to allow for keywords to be searched for
By using the search for function of Nano I came across this string which is great, since in order to exploit something you need to know what your exploiting, the second result was, "linux version 2.4.18-MIPS-01.00 (john@pd-1-server) (gcc version 3.4.6-1.3.6) #7 Thu Jun 21 16:42:13 CST 2012".
After searching the kernel version and the word vulnerability into a search engine I discovered that there was a pretty spicy vulnerability, CVE-2008-1673 to be extact, which allows for a attacker to achieve Remote code execution(RCE) or crash the device causing a denial of service attack(DOS), Thank you John.
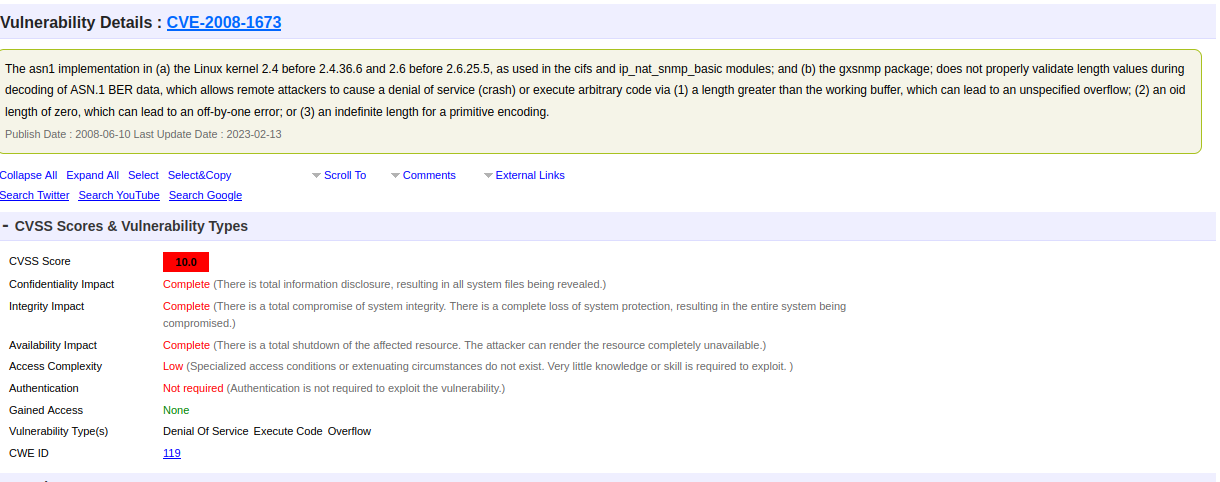
figure 12- CVE database page for CVE-2008-1673
With some more searching im positive that a Proof of concept(POC) of this vulnerability could be found which could allow for a direct attack against this device, while saving time by not having to develop a exploit myself.
Reflection/conclusion
My main goal with this post has been to highlight not just my successes but also the countless failures even in a straight forward project such as this, as I think that's really missing from this space a lot of the content I have seen so far only seems to show the success in a well cut 20 minute youtube video and does not touch on the fact that most of the time spent in this project was debugging and head-scratching.Even the seeing simplest problems, Looking back at when I started to learn that what would have been useful to me to show that everyone makes them regardless of skill or experence, it seems wise to include what I would want out of this content in my own content.
I would consider this project a major success and will continue with projects such as this one and searching the firmware for a vulnerabilities such as CVE-2008-1673, that could possibly be exploited on the device for futher access.
Please use links below if you would like to contact me.