Introduction
Having not worked with enough muppets in my summer job, I decided to create my own sock puppet("sock account") for three main reasons.
1. I follow a lot of politics discussions and various worldly conflicts so having experience to notice when a account is a sock or when it is a real person would be immensely valuable.
2.Like all my projects, I find it interesting so im going to do it since, it also follows on from my last project here
3. I get to browse twitter without feeling guilty about not working(bonus)
For ethical reasons I won’t be actively engaging with this account, its merely for eduction purposes only.
Ethical considerations
As someone who seeks the reasoning of the world, the how and the why, the logic behind peoples choices. I’m fascinated by ethics particularly of complex topics such as intelligence gathering through means likes Sock puppets.
Which is ethically wrong thing by betraying someone's trust through a elaborate set of manipulations and lies but for correct reasons (gaining information to aid people in need).
Before the exploiting of devices and the questioning of life choices can begin we must first find a target device for this project.
As a example of this Ethical dilemma in early 2021 a blog called a gay girl in demascus was 2011 documenting the life and the experience of Amina Abdallah Arraf al Omari.

figure 1- image that was used for Amina Abdallah Arraf al Omari
A Syrian teacher who happened to also be a lesbian living under the Asad dictatorship, during the 4 months the blog was active Amina became prominent and respected figure for within the LGBTQIA+ groups both within Syria and across the globe, even writing for
another well respect Syrian news site that actively promoted lesbian rights under the name "Lez get real".
A man called Thomas Jarvis Macmaster claimed too have created Amina, so he could discuss middle eastern politics without being seen as another ill-informed American,despite the fact he also stole photos from a British women to pass them off as Amina, engaged and maintained a inmate 6 month long relationship with a french-candian women named Sandra, which Mac masters claims he had not intention of doing and it "got away from him".

figure 2- screenshot of A Gay girl in Dmascus blog
Rather comically the newspaper Lez get real, that Amina occasionally wrote for also happened to be a sock puppet account, created by a retired American construction worker, Tom Graber who create the identity of Paula Brooks, who was a Syrian lesbian living under Asad who was also rather conveniently deaf, so she couldn’t do any interviews with reports over the phone
While many believe Macmasters and Graber actions actively hurt the movements within Syrian through there exposé stealing the limeline as the media focused on them instead of real issues while also making the community even more of a laughing stock within a country that already actively hates them.
But they need seem a net force for good with Macmasters owning up to his mistake, but equally it was likely only a matter of time before he was found out so take that good act with a pinch of salt.
So while their technical ability was sound they lacked a code of ethics. Contributing heavily to the events above.
Code of ethics
As the old saying goes, "there is no honour among thieves" but there is a code of ethics particularly when it comes to the social engineering aspect of OSINT, which is what Macmasters and Grabers failed to grasp.
While through my research I haven’t located one singular code of ethics that everyone within the field seems to follow and agree, if anything the opposite but the general census is
- Only collect relevant information to the investigation (also a legal aspect in the UK due to the Regulation of Investigatory Powers Act 2000 (RIPPA) and Data Protection Act 2018 (DPA)).
- Do not negatively manipulate, threaten, or make others uncomfortable in any way, unless specified by a client due to unique needs and testing environment.
- Reject any engagement, or aspect of an engagement, that may make a target feel vulnerable or discriminated against. This includes, but is not limited to, sexual harassment, offensive comments (verbal, written, or otherwise) related to gender, sexual orientation, race, religion, or disability; stalking or following, deliberate intimidation, or harassing materials.
- Additionally, lewd or offensive behavior or language, which may be sexually explicit or offensive in nature, materials or conduct, language, behavior, or content that contains profanity, obscene gestures, or gendered, religious, ethnic, or racial slurs are all to be avoided. Employing any of these tactics reduces the target’s ability to learn and improve from the engagement.
Which the Macmasters seems to treat like a to-do list, while not ill-tented in anyway it still caused major emotional and physiological damage to Sandra who he engaged into the relationship which is clear to see 2015 documentary the Amina profile.
A augment for mac-masters could be made on the grounds that he was an inexperience person who is in way over there head, that you might be able to accept and somewhat understand but mac-masters, next action is truly inexcusable, and smashes through point number 3.
Fake kidnapping
On the 6th of June 2011 a blog post was made on A gay girl in Damascus by a person claiming to be Amina cousin “Rania Ismail” which alleged that Alima had been kidnapped by pro asad forces that were well known to murder, torture and rape victims. And leading the entire community surrounding this blog including Sandra, to assume Anima had met the same fate.
This only came to a end when Sandra contacted the US foreign office, since Amina, was supposedly a American citizen, having grown up in the states before moving back to Syria as a adult.
How to set up a sock puppet and maintain opsec
Now that we understand the ethical implications of lying to strangers on the internet, we also need to learn how you do it and not get caught. In our case through a sock account ,luckily the internet is full of people with room temperate iq’s, who do get caught and we can learn from their mistakes.
First is and always a reliable source for screw ups, are US federal agents,personally I think this one is the crème de la crème of poor opsec.
Lets go over the mistakes they made.
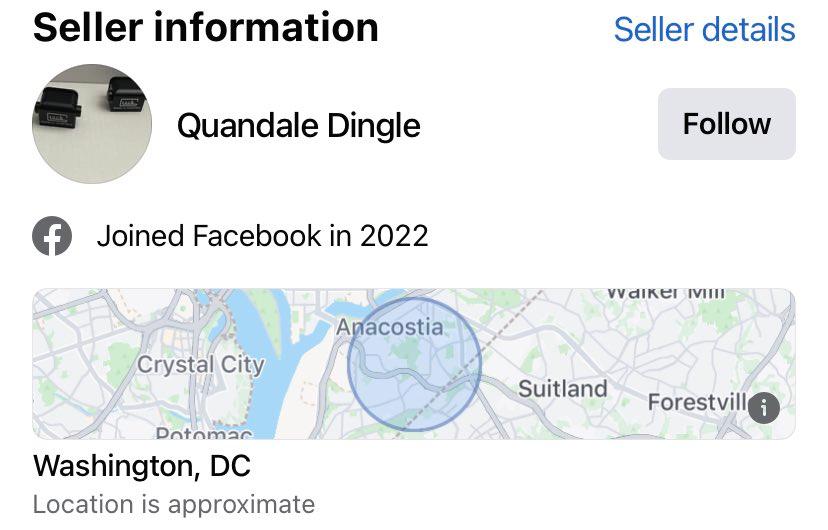
figure 3- facebook marketplace post for illegal firmarms mod
- Facebook is one of the biggest known data collectors on the internet, and it hands over any and all data that is asked for. (Note: While not valid here since law enforcement isn't going to request data on themselves, it's worth pointing out this fact).
- Quandale Dingle is the name of a high school football player from New Jersey and also a meme that was popular in early 2022. Unfortunately, I couldn't validate what part of 2022 the user joined Facebook.
- The seller left the location on which just so happens to be slightly above the Defense Intelligence Agency, the part of the American Department of Defense (DoD) that handles intelligence gathering. From research, it doesn't seem like they handle domestic issues; I believe that's the Bureau of Alcohol, Tobacco, Firearms and Explosives (ATF) job.
At least they used a alias for the account *cough conner brain Fitzpatrick.
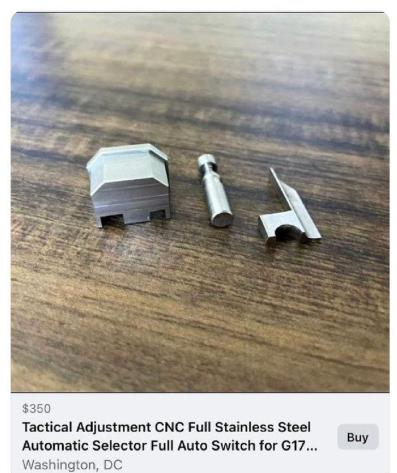
figure 4- image of illegal mod
this photo shows the defence intelligence agency on the left, with the road highlight in the Facebook post circled in red(note the "location is approximate" text in the image above)
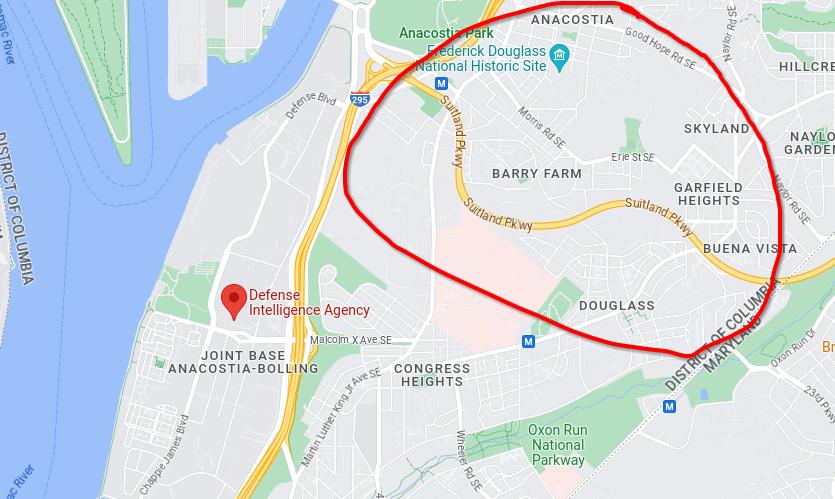
figure 5- approximate location for seller shown on google maps next to the DIA building
I saw a couple of posts eluting too the material on the table and the amount of light viable at the back, they made the assumption it was a conference room, while its certainly possible I don’t have enough information to say positively.
I could use a tool such as suncal.org to try and match up the light patterns to establish what part of the building the photo was taken from, if I had access to the data and time of the posting(assuming the photo was taken around the same time the post was made.
How to fix them
All hope is not lost for our glowing friends though these mistakes can be easily rectified.
1. Turn your location off/don’t listen your location if possible(in this case just leave a address the description or say "dm for more details").
The trick with setting your location is too set it near enough that it seems legitimate but not close enough that your not exposing your self, for example If I someone in the UK were posing as a Texan from Dallas, which is 6 hours behind the UK, im going to give the game away instantly if Im tweeting a picture of my breakfast at 2am.
Personally I think the best way of managing this is to take a leaf out of NASA’s Mars missions book, where the teams work by the time it is on Mars instead of earth time, that way they are awake when the rovers are and sleep when its dark there so the rover sleep(ignoring RTG'S) and other powersources which I just had to delete a few paragraphs about because im a massive nerd who likes to ramble about stuff their interested in, hence this blog.
The neat way NASA gets around this problem is by giving all its staff special watches which show both the time on Mars and the time on earth. We can do the same thing by setting a extra clock widget on a phone. While alarms would also work but they create patterns and patterns of posting aren’t very natural which makes your account stick out very clearly as a sock.
2. Pick a name that fits with the area your sock puppet is from, maybe you could use a baby name generator if you have to, but not from your favourite meme, so the first thing that pops up when you search that name isn’t a know your meme page.
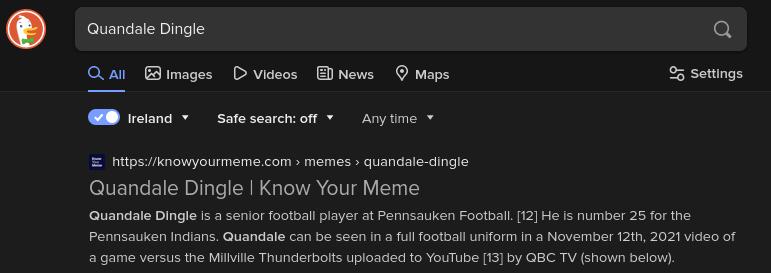
figure 6- search results for the term "Quandale Dingle"
3. when taking photos or videos its important to pay attention to aspects such as lighting or what can be seen in the video, make sure the current time or weather matches up with what your saying.
Build-A-Person
Research before I did anything I researched the topic through books, articles, courses,youtube,films.
As a self taught computer nerd upon till this year when I started my degree, you can really teach yourself anything if you have a library card or internet connection, all you need is time and the interest in a topic.
Unfortunately most people myself included have to work 40+ hours a week, while being luckily if you only get a few hours a week to work on projects this can be a tall order hence the reason this project has taken me best part of 3 months instead of my usual amount of time. Not the best for trying to realistically age and grow a sock account.
So I decided that I make would a twitter account as that's my target demographic for this project.
During the research phase I found a interesting article here another interesting one by a researcher Garret Mickey its a few years old but the advice and services mostly still ring true, but does relies on known data collection services e.g. Amazon, Google, so not the best for privacy reasons.
Garrett suggests a website called Fake Name Generator here ) to flesh out the socks identity as well as including things such as browser user agent,what type of car the person drives and a real email address and account.
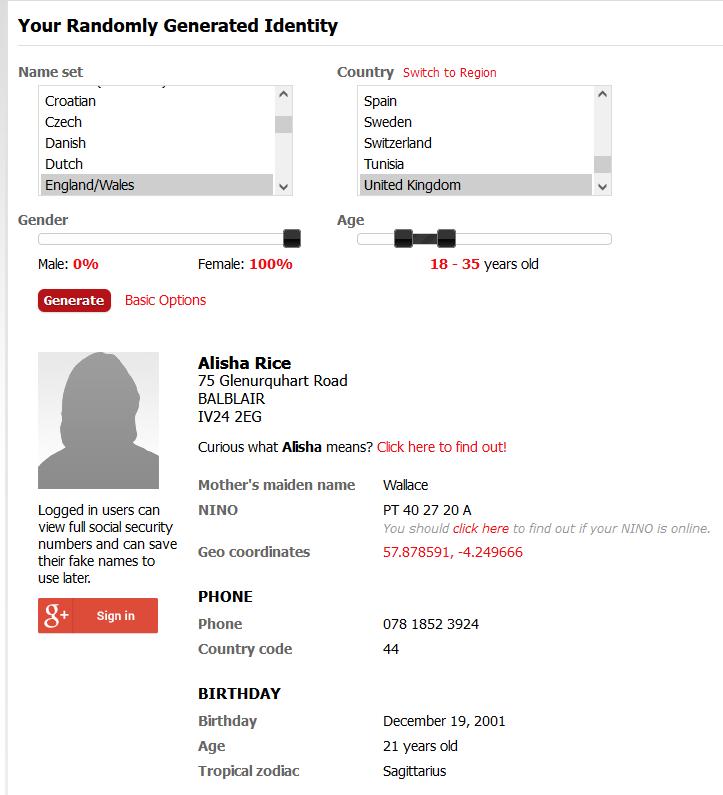
figure 7- fake name generator
Meet Alisha a 20 year old from Inverness, Scotland due to its location, the internet connection is unreliable so, unfortunately Alisha as a minimal digital presence, up until she moved to south Wales.
Now we have a name but we still need face, but as mentioned above with Macmasters, hugely unethical to just scrape some poor souls, instagram, this is where the website persondoesnotexist
here
comes in it generates a profile picture by feeding a large data set of faces through a generative adversarial network called StyleGAN in order to create a endless stream of fairly passable face such as this one, at just a press of a button.
While some people claim to have issue with certain websites I never encountered these, but can be simply fixed by adding sunglasses to the image through photo manipulation software photopea,GIMP,photoshop.

figure 8- generated photo of "Alisha" and her friend
This image produces zero results when run through a reverse image searching service such as Tineye
( Yandex is better for facial recognition searches apparently but never tested it myself)
but this Tineye proves the point.
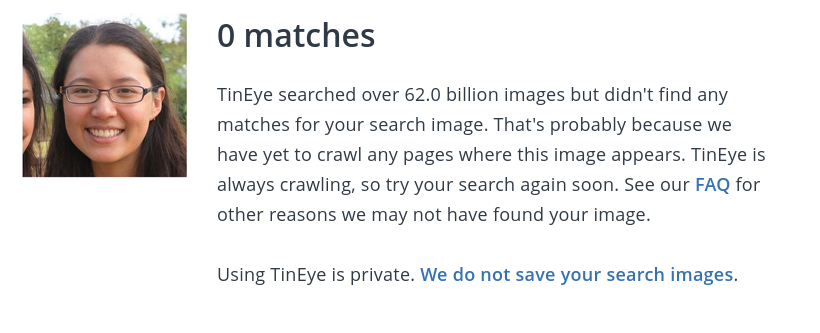
figure xx- reverse image search of figure 8
- There are a few minor issues with the photo I only noticed as I'm writing this:
- Ally’s left eye and its shadow don’t quite match up
- Her right ear ring seems to fade out of existence
- A strand of gravity-defying hair across her Anti helix
- Hairline isn't straight
- Her friend has soulless eyes that are staring
- The left arm of her glasses seems to bend or just be nonexistent
this took me properly about 10-15 minutes to find a decent photo that I didn’t skip over accidentally, and doesn’t have that uncanny valley vibe going on.
The reasoning behind this photo is of course that fact the person in the photo is a girl who looks like she is in her early 20’s, a nondescript background to add legitimately to the photo.
Also I chose friend over something like sister or cousin because its much easier to get away with never mentioning in a friend than a sibling or familiar relation, following the logic of if you have to lie, lie in the smallest insignificant way possible as it reduces the change of putting your foot in it later and getting caught.
But the key aspect that separates this photo from other AI generated photos is the second person on the left hand side of the image, so when the photo is cropped for a profile picture it simply looks shed been cropped out due to size limit like so.
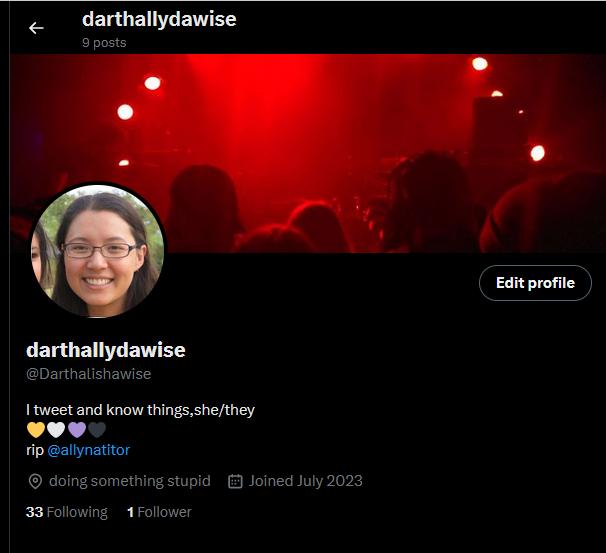
figure 9- sock twitter account
A quick explanation of what's in the in photo.
Few minor details added to the bio
- Quirky Quote Small character detail here
- Displaying Non-binary colour as hearts common on twitter
- A account that no longer exists, which can help explain away why the account is so new, perfect timing with Musk burning down the platform as well.
- A few posts, mainly quote tweets and videos.
The ideal account needs to be aged for around 9-12 months typically being a private account during that time, before its ready to be used but I don’t have that amount of time so 2/3 months will have to do.
As for the background image, that was also taken at the same concert, and never posted anywhere online, so no way of tracing back to anywhere.
However I would be a fool to put my trust in someone else's work and not prepare the image by renaming it and stripping the exif data.
But just to be sure we can it our selves.
Since the file name refers to the time and date of when the photo was taken, in the format of year,month,day,hour,minutes,seconds, in 24 hour time.

figure 10- PNG image with date and time in the filename
e.g. 2023, 03, 29 , 8:01:03pm
Super neat trick super basic but one I never seen mentioned before,
for example this is a a photo from the same black honey concert that has been posted previously on the account, since we know what time the band came on and we know how long each song is since the album is public record we can tell which song was being played(it was Charlie bronsonon if you were wondering).
Especially since tools such as exifviewer and fotorensics are easily fooled by simply screenshoting the image which is what I also did as a extra precautionary measure.
For example
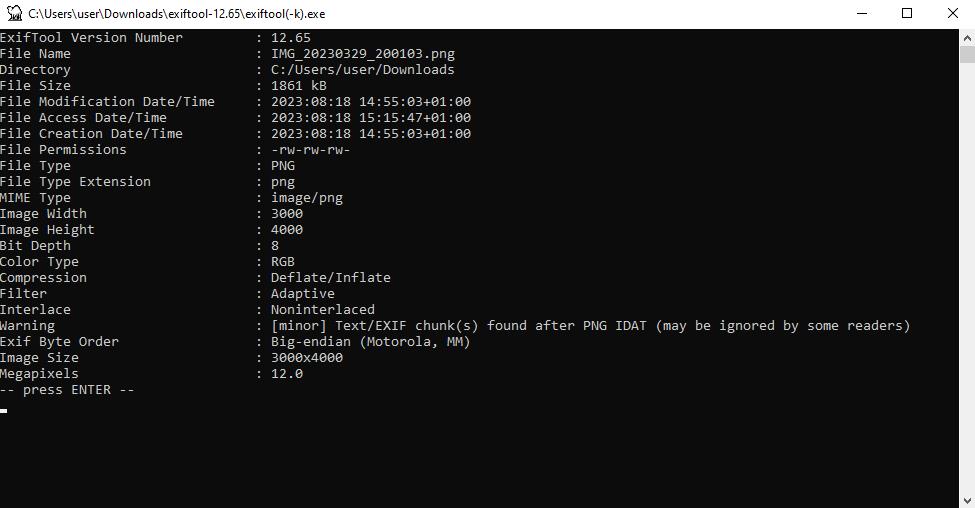
figure 11- exiftool results from image pictured in figure 10
the file name clearly shows the end of march with the data and time, the file creation attribute showing the middle of august.
Just to make sure it isn’t the program a second tool is used which confirms the first tools results.
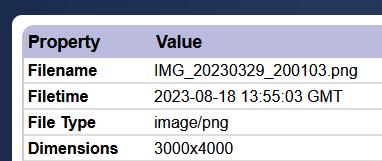
figure 12- fotorensics results from image pictured in figure 10 to corroborate figure 11
Setting up the email.
For this project I chose to use proton mail, for a few reasons while we don’t need this account to be super secure its still wise to have a certain level of protection from a security point of view.
- Reasonably private: No selling of data to 3rd parties
- Comes with a feature called "Mailbox Password," which is a second password handy for not saving to a device for security reasons but allows the account to still be secure through the email and password.
- Has 2-factor authentication.
- Doesn't require lots of personal data to sign up with, such as a secondary email, phone number, birthday, or location.
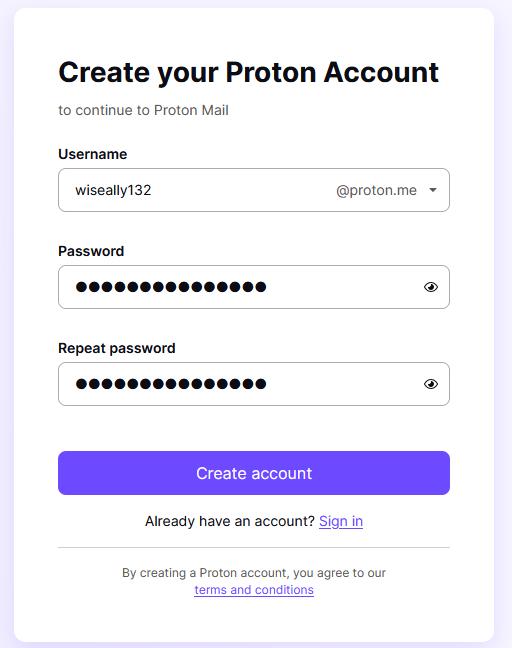
figure 13- protonmail signup page with details filled out
While proton mail isn’t 100% private as they do occidentally comply with Swiss law to hand over data but, it’s secure enough since I don’t plan on raging against any government machines in my spare time.
But Proton does state in there terms of service they do everything they can to stop requests and give the least amount of data possible data
"Under Article 271 of the Swiss Criminal Code, Proton may not transmit any data to foreign authorities directly, and we therefore reject all requests from foreign authorities. "Swiss authorities may from time to time assist foreign authorities with requests,provided that they are valid under international legal assistance procedures and determined to be in compliance with Swiss law".
Proton also publishes a transparency report of how many orders they receive,contest and comply with
While they are debates within the privacy community about protons actual privacy, but in my opinion, you got two options, go full tin foil hat and self host everything yourself, or accept people have to obey the law,(bulletproof hosters, are a separate matter I won’t get into due to the nature of the content they often host.)
Another reason why I chose to use a permanent email address instead of just getting a temporary one is, due to working doubles, looking after relatives and other life factors, there has been multi-week periods, where I haven’t been able to work on this project, so if I need the account for what ever reason such as resetting the password, I can get back into the account and not lose weeks of work.
Now we have the backbone of our sock set up we can setting up the social media's, like Twitter
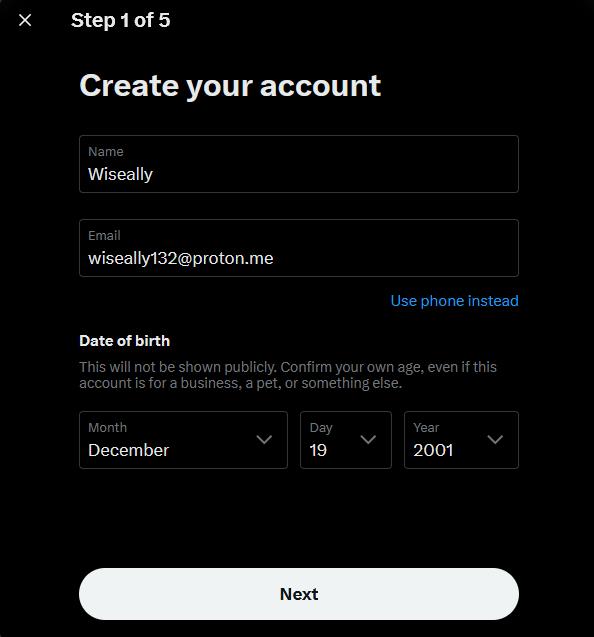
figure 14- X's(twitter)account sign up page
you may or may not have noticed the fact you no longer have to provide a phone number to sign up to twitter, which saved me plenty of time, avoiding setting up that, especially since mint mobile is no longer a option, for a cheap prepaid virtual plan.
This change also makes the twitter onion link viable again, if you want additional privacy
here(require tor)
cookies
Alright, let's do this one last time, Turn off any cookies or personalision options you can find, it’s ones of the easiest mistakes to make, and you really don’t want to ruin your opsec, and all hard work, by the people you may know section, Ask me how I know!
figure 15- X's(twitter) cookies banner
Rejecting cookies is a easy first step, While its debated if it does anything to stop companies such as Meta,twitter(x), from tracking you, or selling your data to advertisers, like their suppose to, However they do stop sites from remembering preferences,account details,automatic login.
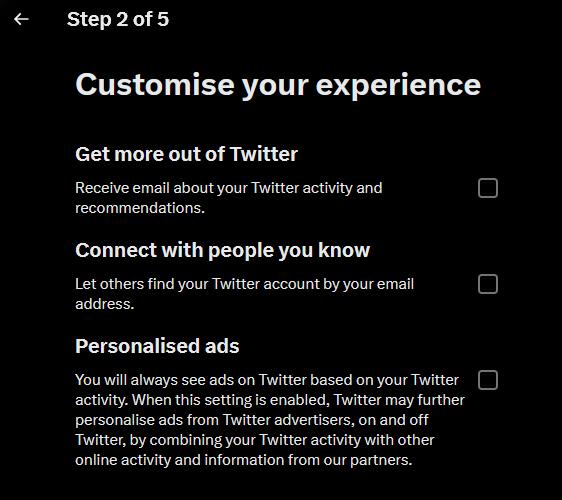
figure 16- X's(twitter) data hadling and processing customization page presign up
As I mentioned earlier about the "people you may know" section on facebook, the second option in the image serves the same purpose, allows your account to be searched for by email,
For example say you use your personal email which is attached to your personal twitter account, to sign up for a account on a different website and send a investigator a threatening message, all the investigator has to do is search twitter, for a account attached to that email, and then they can find your personal account which is also linked to that email. that's why its important to disable these options.
With some more searching im positive that a Proof of concept(POC) of this vulnerability could be found which could allow for a direct attack against this device, while saving time by not having to develop a exploit myself.
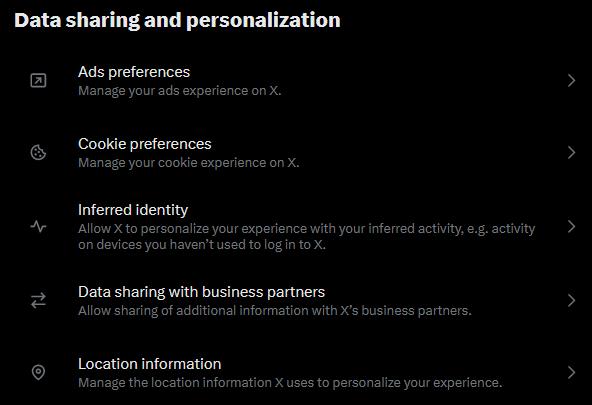
figure 17- X's(twitter) data hadling and processing customization page post signup
Setting up the interests
Luckily with this project I have the benefit of being able to use some of my own interests, here
so I am able to make the account look more legitimate, essentially because I know what im talking about, which saves a lot of time on research of these topics.
Personality
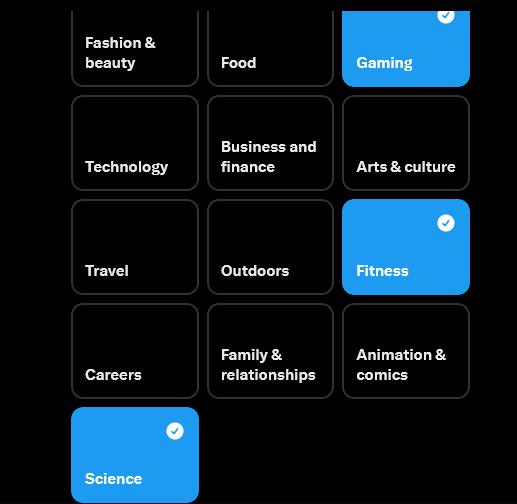
figure 18- X's(twitter) suggested areas of interest
Naturally this depends what area you where you sock account needs to be place in, a account that talks about props and Martian planetary geology, isn’t going to fit into a conversation about the Libyan civil wars very well.
following some accounts
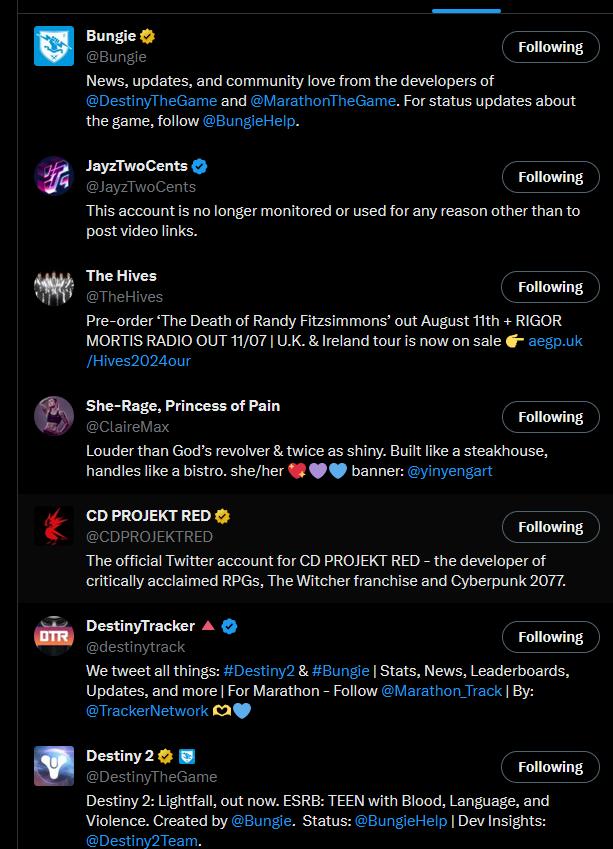
figure 19- accounts relating to accounts interests on X's(twitter)
These accounts are fairly big, but most common within the communities, there I followed 34 accounts in total but couldn’t get showing them all here to look right, so heres a selection of some of them.
But they are a mixture of science,music, and gaming, with a focus on, rock music,Destiny 2 and Mars. With one or two fitness accounts.
Browser add-ons
Similar to my last project setting up the hardware/accounts is the easy part, the hard part comes from keeping your opsec secure.
This segment will focus on firefox browser add-ons for the pure reason of that's what I used and where most of my experience comes from, however most add-ons do cover multiple popular browsers such as chrome,brave,opera, and other browsers such as Edge, or have equal counterparts.

figure 20- say the line bart meme about private browsing
Remember incognito mode is only handy if you want to "shop for gifts for your wife" not so much if you want to avoid large tracker networks over the internet.
Besides privacy the second best browser feature would be translation, while twitter itself does offer that natively for text but not for images, or other websites. So A Optical character recognition(OCR) addon maybe a wise additional.
Add-ons to control video playback speed are key when trying to systematically comb through a video looking for clues, such as identifiable items,people or locations in backgrounds or reflections of videos, for example video from a war, being able to slow down a video to 0.07x speed to search for insignias which may implicate a certain faction in a attack.
Or a more relevant use case for this project would be to speed up video, for example speeding through 10 minutes of shaking concert footage, to try be able to discern what venue the concert was held at.
The Wayback machine addon allows for snapshots of pages to be saved, so they can be viewed at a later date, While it’s main use is for Historic preservation, it can also be used for osint, also allows you to submit your own links to be saved.
Google also allows you to view cached version of websites
figure 21- Google search result showing three dots
by clicking on the three small dots then scrolling down and pressing the cached button
figure 22- three dots menu showing Cached button
As for the for more privacy focused addons, any standard trusted tracker blocker can be used such as
- Privacy Badger
- U Block Origin
- Consent-o-matic
- Firefox Relay
- Terms of Service; Didn’t read
- User Agent Spoofer
These addons all serve a similar service of protecting your real identity by obfuscating your activities, or information through false data.
Im personally a fan of language tool to since its a free and open source spell checker, that can be self hosted if you really want.
Having a secure and private spell checker is critical since pre-installed ones inside of chrome and edge transmit everything that is typed back to home servers, including passwords and other critical, private information you don’t want being hijacked or leaked.
Conclusion
Ultimately the main thing I learnt with this project was, you can't do good work when your stressed, sometimes slowing down and taking a break results in higher quality work, having said that think this project was a success but could have been better not going to lie.
I Do love projects where I get to put my knowledge into practice, as can be seen with my previous works, While I did not have access to the resources I tend to have, in both a financial and time sense, the back to basis approach of extremely limited budget helped me relearn some skills I had when I was younger and in a similar financial situation, which I found very enjoyable , and only slightly ruined by sleep schedule by staying up after work, to do this.
One of the only downsides being I really underestimated how little time I had over this summer, I natively though I could do 2-3 projects over the past 3 months, when in reality I barely managed to do the research for one and this project.
Due to the sole fact of quality, I could have easily done this project in half the time, but it would be terrible quality, and that isn’t the type of work I want to be associated with to be honest,
I tend to spend about a week or so going through my project to make sure, everything I say is correct, comes across in a easy to understand manor, because im very Dyslexic and like to ramble.
With another week easily being spending converting this (at time of writing 22 page, 4,219 words long write up) to html, to be published on my blog.
And after all that is done all I can say I don't think its perfect by a long shot, but equally I do have a tendency to hold my self to ridiculously high standards, which is something im working on.
Editors notes always check your character encoding is set properly before you spend hours manually copy and pasting in punctuation,
One double quote cost me about 2 hours, I absolutely love computers.
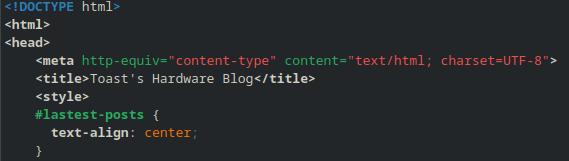
figure 23-html error causing the character encoding to not function properly
Please use links below if you would like to contact me.
